A hard and fast method for reducing Active Directory Administrators members.
Introduction
Anyone that has gone through any security hardening process can confirm that simply saying something was done incorrectly does not mean that you can just apply suggested remediation steps, especially in a mature environment.
Take recommendation Appendix E, F and G from the AD DS Operations Best Practices for Securing Active Directory for example, even though I agree with all of the points, just removing user accounts from the Administrators groups (Enterprise Admins, Domain Admins or Administrators) without addressing the application requirement could have a significant impact on
daily operations.
Based on my experience, the biggest reason why user and service accounts were added to Domain Admins and the like was that default delegation model in Active Directory lacks an appropriate group that just gives server/workstation administrative rights.
This article describes the process of creating these delegation groups so that members of Domain Admins etc. can be removed without any impact, drastically increasing Active Directory overall security. It must be stressed that this is an intermediate
process, the lesser of two evils if you will and that these other issues will be addressed in future articles.
Creating Global Administrators Delegation
1) WMI Filters
Create WMI filter that will identify the three device types. In the article two of these, All Servers except Domain Controllers and All Workstations will be used. This allows
delegation policy to apply to the correct device type dynamically.
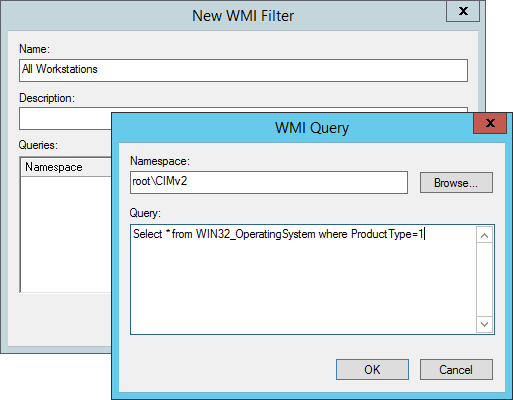
a) Create an All Workstations WMI filter according to company naming convention
Select * from WIN32_OperatingSystem where ProductType=1
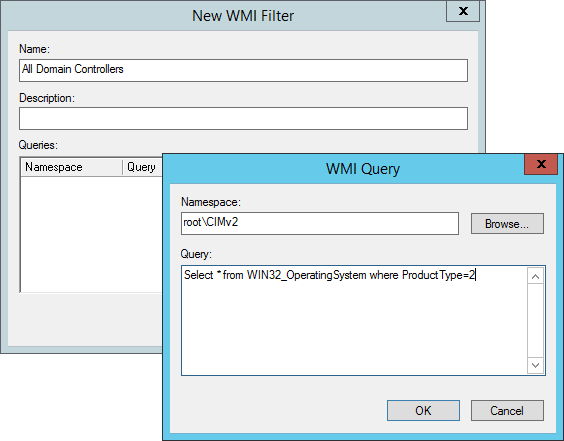
b) Create an All Domain Controllers WMI filter according to company naming convention
Select * from WIN32_OperatingSystem where ProductType=2
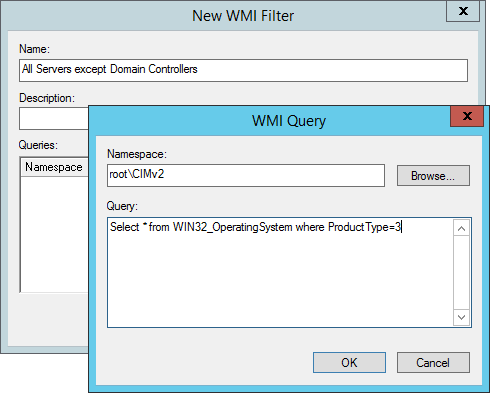
c) Create an All Servers except Domain Controllers WMI filter according to company naming convention
Select * from WIN32_OperatingSystem where ProductType=3
2) Groups
Create a group for each device type and a group that will have rights to all device types. These will contain the administrators for each device type.
a) Create Global Server Administrators group, Global Workstations Administrators group and Global Administrators group according to company naming convention.
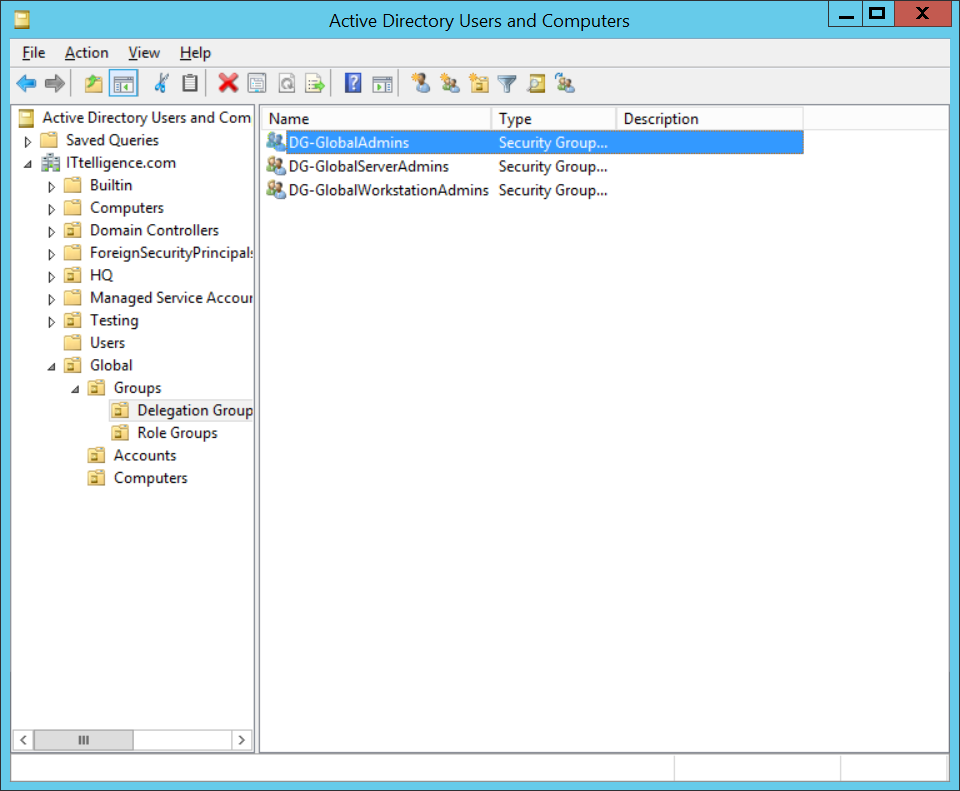
b) Add Global Administrators group as a member of both Global Server Administrators group and Global Workstations Administrators group.
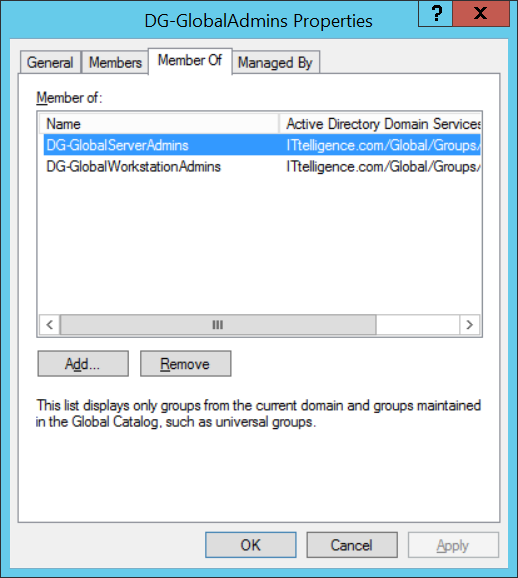
3) Group Policies
Create a group policy for each device type. It should filter based on the device types and will contain the delegation settings.
3.1) Global Server Administrators Group Policy
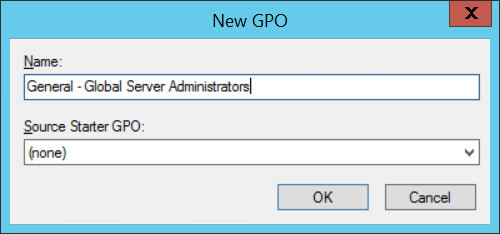
a) Create new GPO and name it according to company naming convention. It will contain the configuration of the Global Server Administrators group.
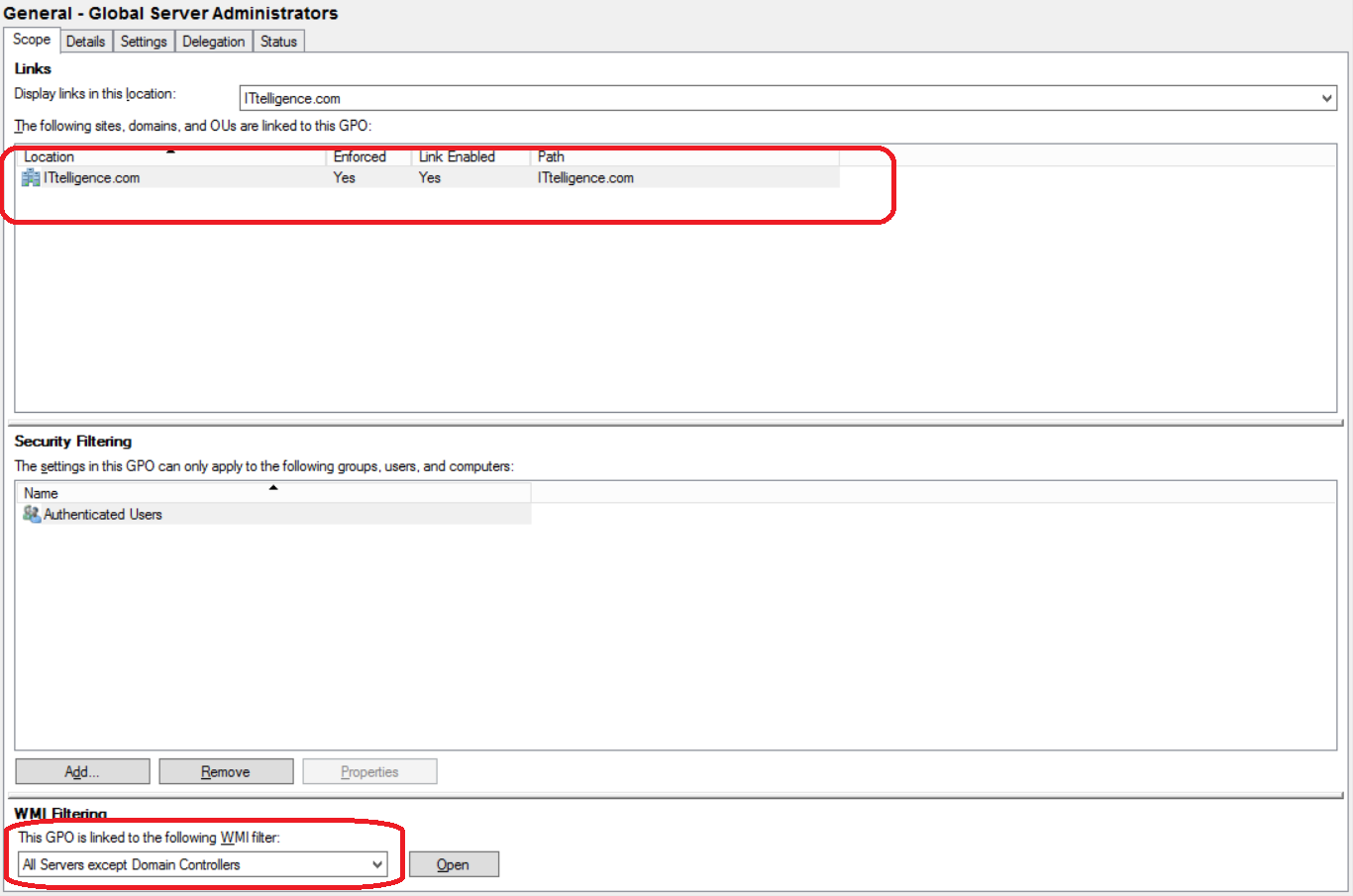
b) Ensure group policy is linked from domain root and that it is enforced. Link the All Servers except Domain Controllers WMI filter to group policy.
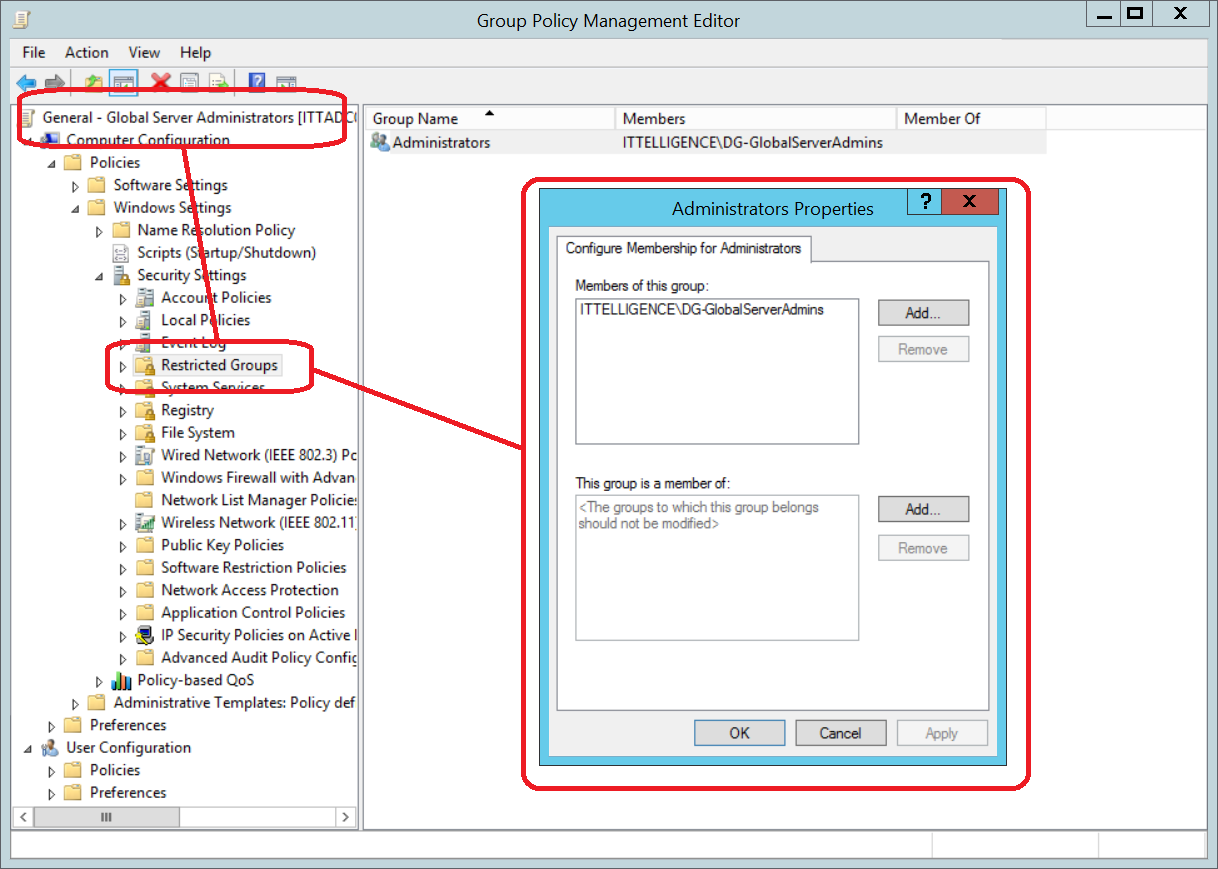
c) Add Administrators group to Restricted Groups and add Global Server Administrators group as a member. This is mainly done for legacy devices.
d) Add Administrators (built-in) group to Local Users and Groups preference update item and add Global Server Administrators group as a member.
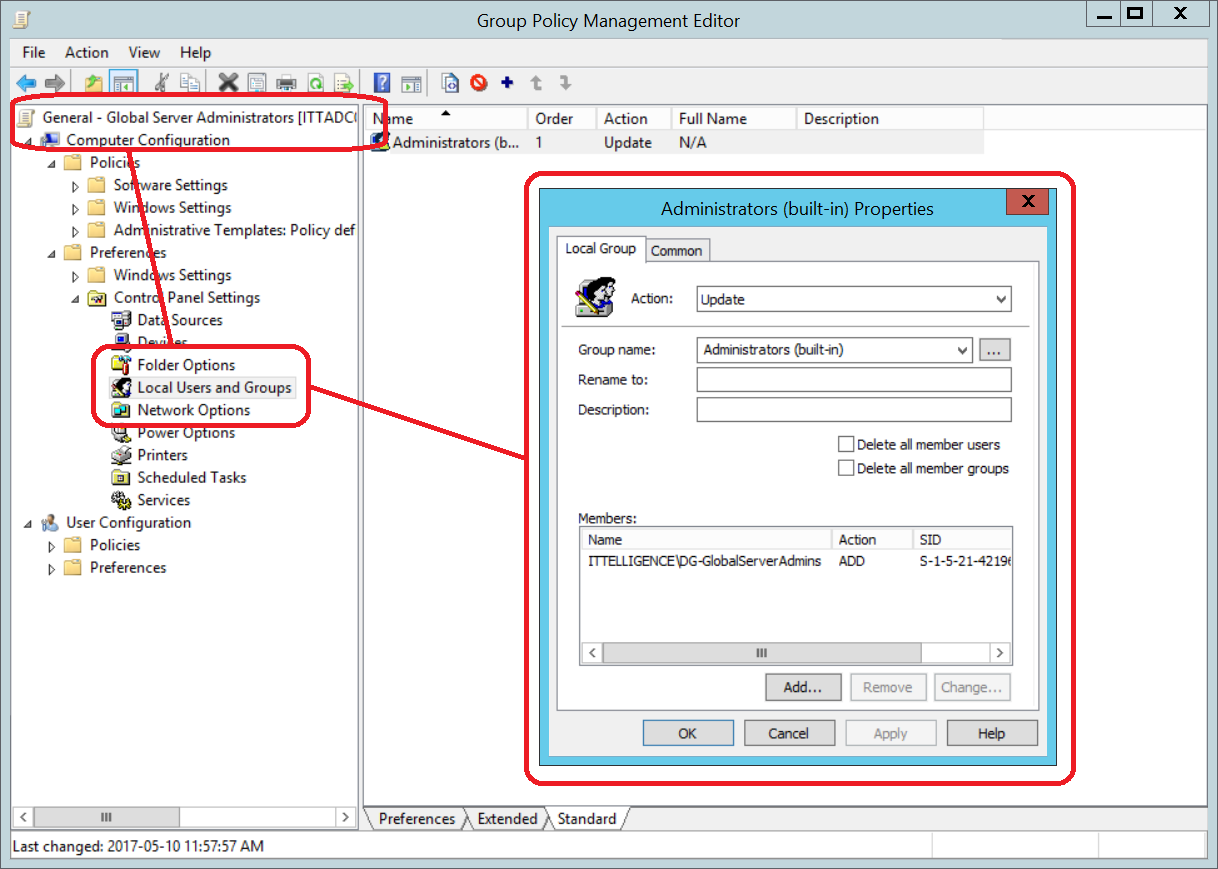
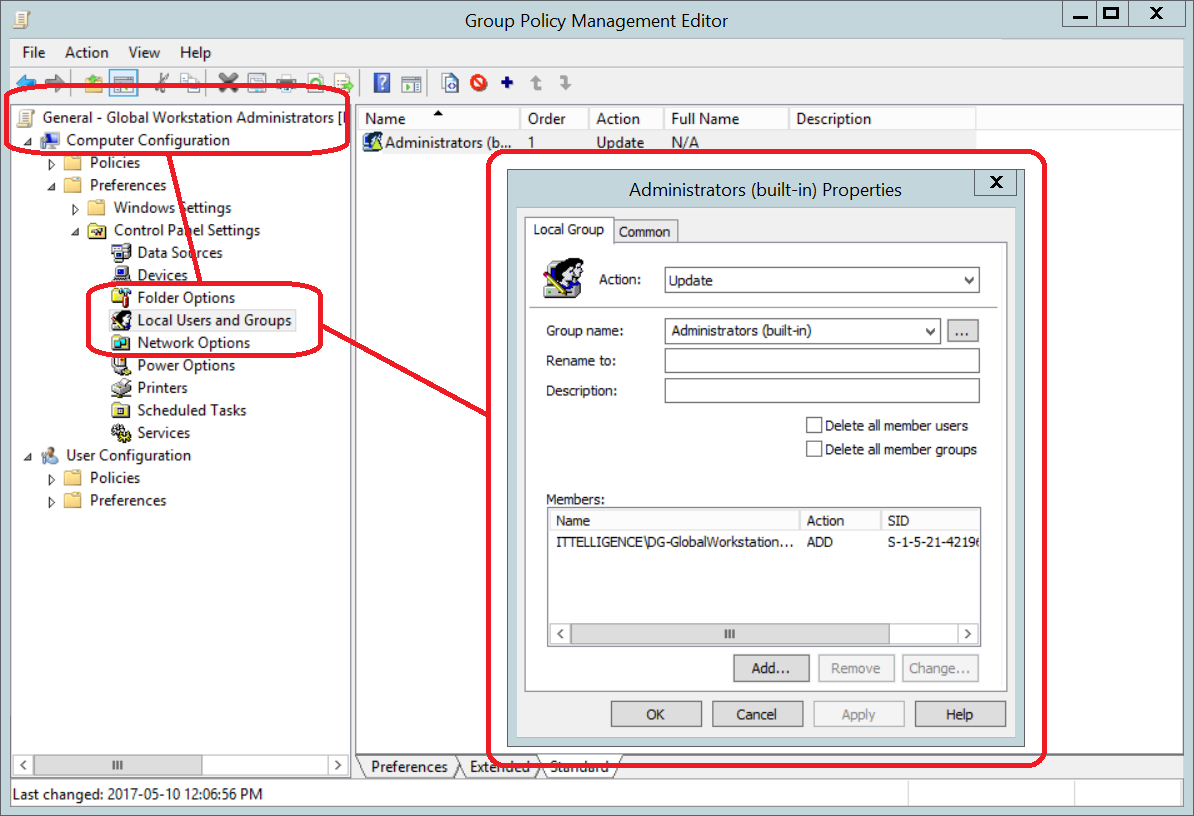
3.2) Global Workstations Administrators Group Policy
a) Create new GPO and name it according to company naming convention. It will contain the configuration of the Global Workstation Administrators group.
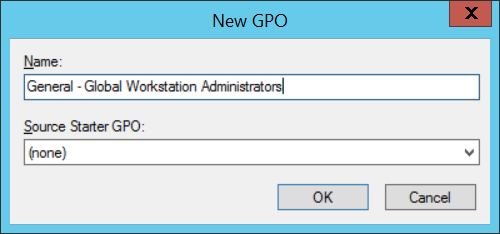
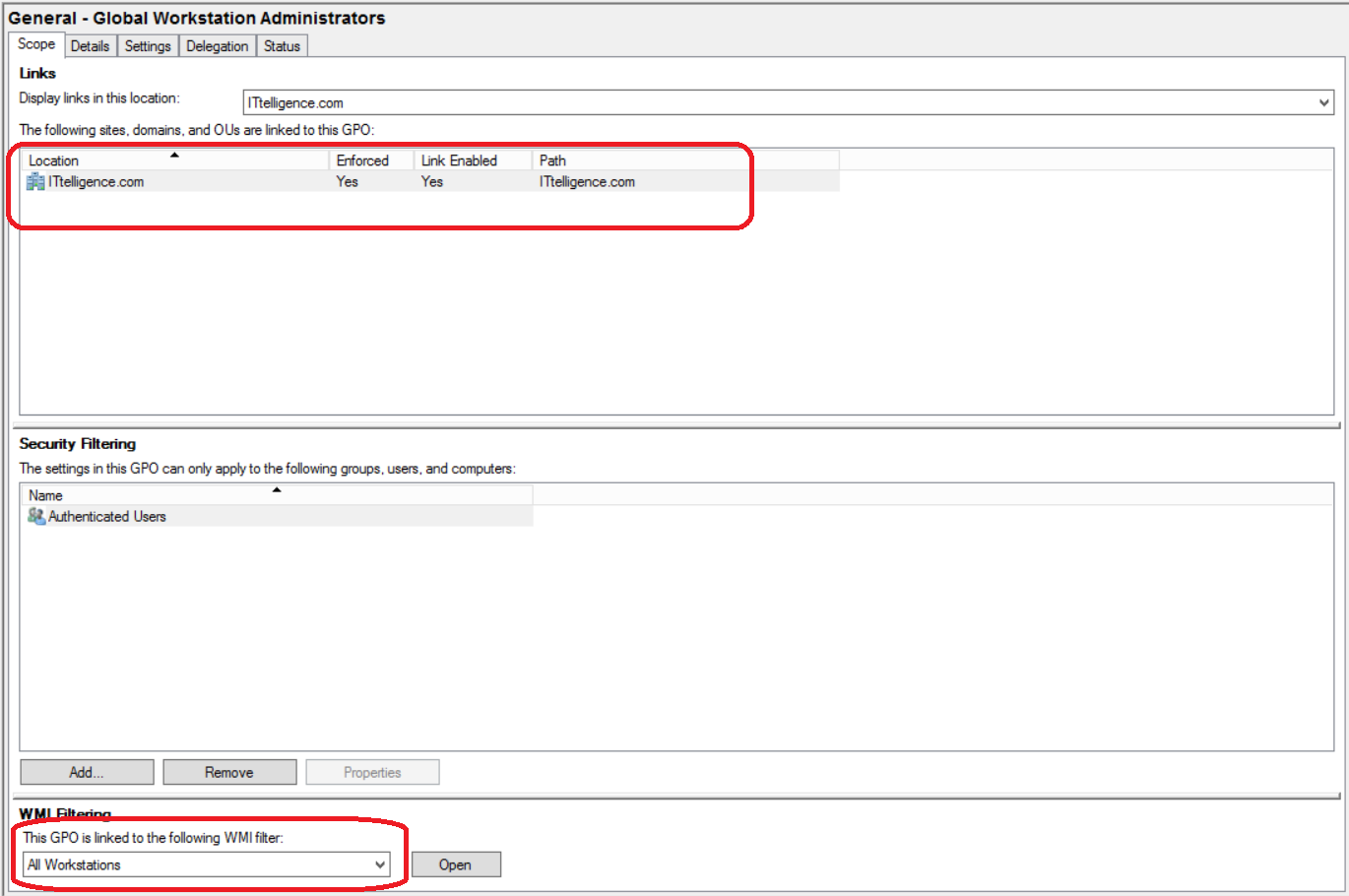
b) Ensure group policy is linked from domain root and that it is enforced. Link the All Workstations WMI filter to group policy.
c) Add Administrators group to Restricted Groups and add Global Workstation Administrators group as a member. This is mainly done for legacy devices.
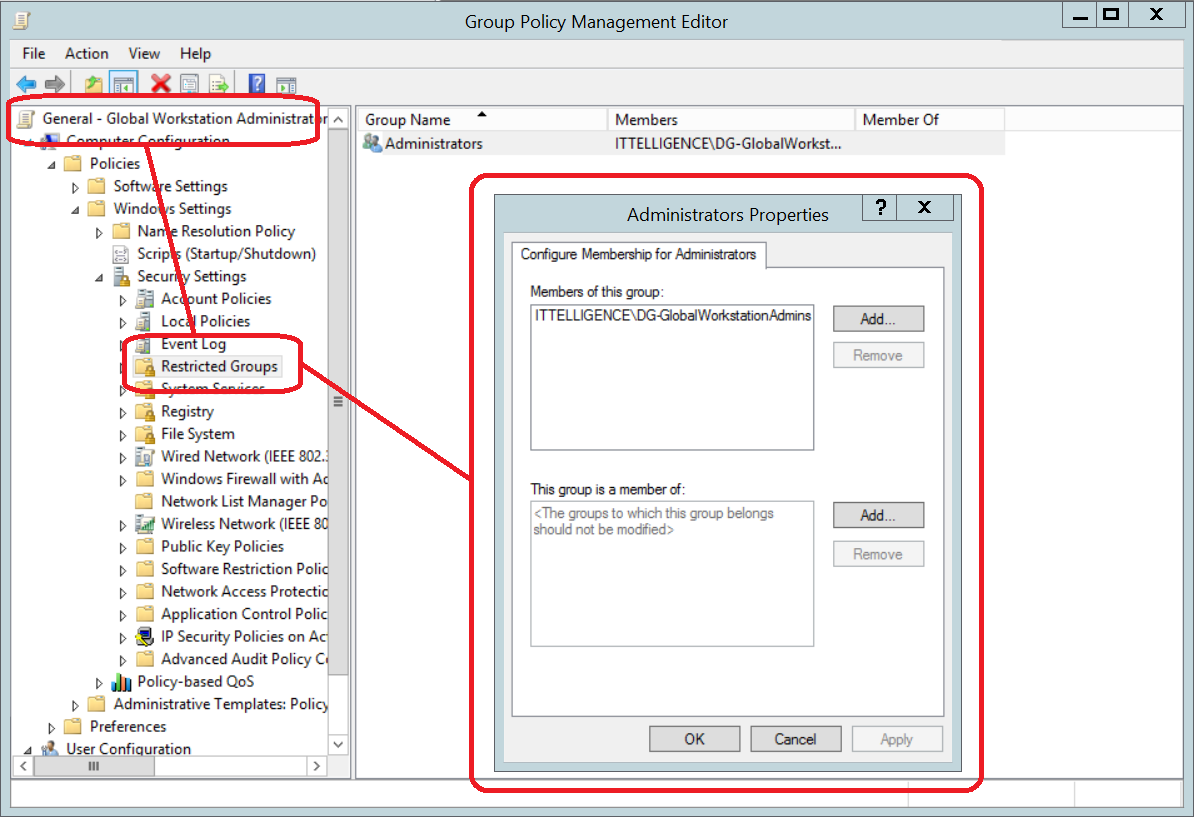
d) Add Administrators (built-in) group to Local Users and Groups preference update item and add Global Workstation Administrators group as a member.
4) Remove User/Service Accounts
At this point, everything is ready to start removing accounts from Administrators groups by following the following logic:
| Account Requirement |
Action |
| Account requires AD rights |
Remove from Administrators groups (Enterprise Admins, Domain Admins or Administrators) and temporarily into Account Operators group until correct rights can be determined |
| Account requires Administrators rights to all devices |
Remove from Administrators groups (Enterprise Admins, Domain Admins or Administrators) and add to Global Administrators group |
| Account requires Administrators rights to servers |
Remove from Administrators groups (Enterprise Admins, Domain Admins or Administrators) and add to Global Server Administrators group |
| Account requires Administrators rights to workstations |
Remove from Administrators groups (Enterprise Admins, Domain Admins or Administrators) and add to Global Workstation Administrators group |
Please note: It is best to add these user/service accounts to role groups as explained in this article:
https://www.experts-exchange.com/articles/29366/Delegation-the-proper-way.html
Conclusion
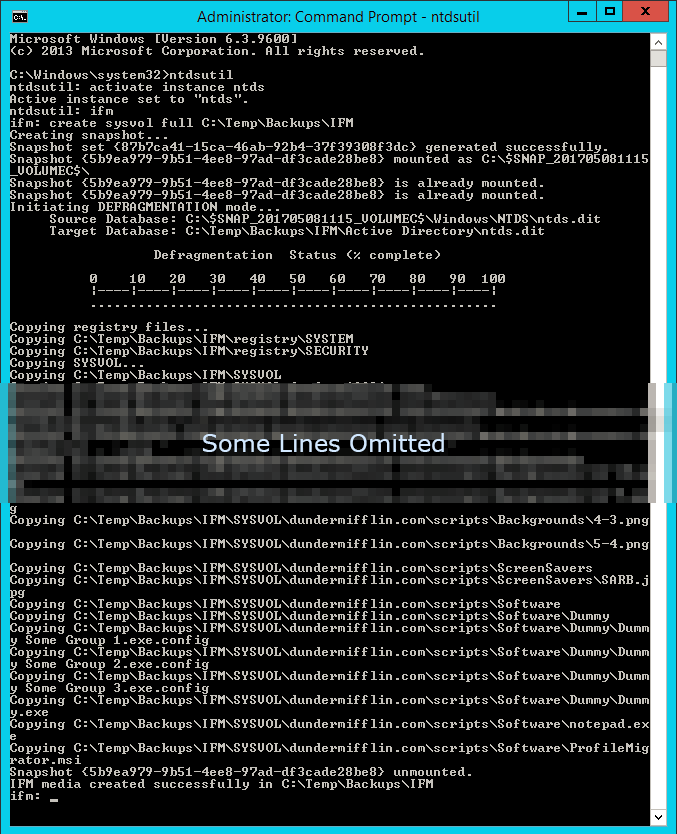
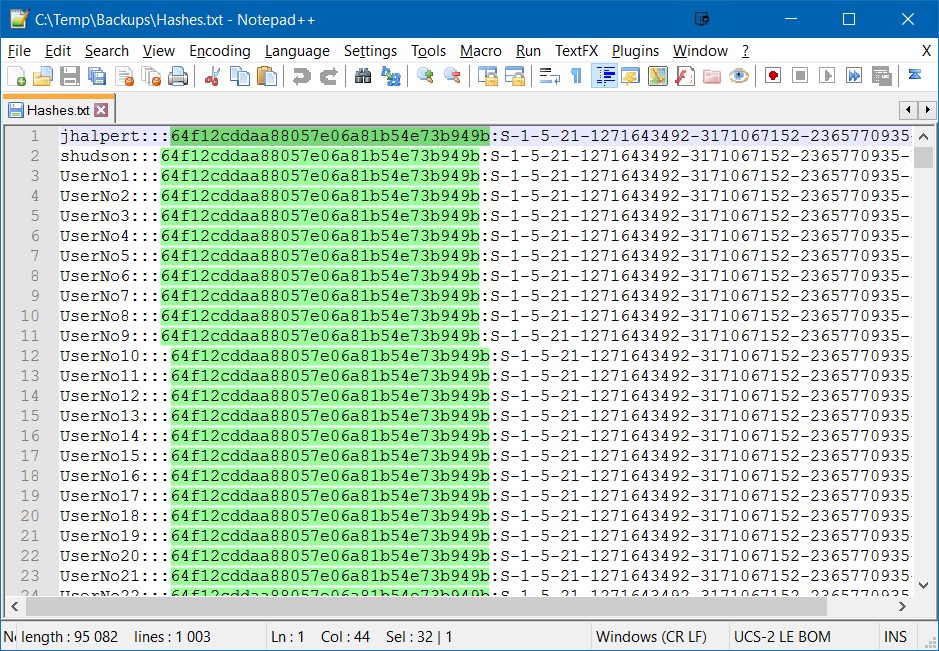
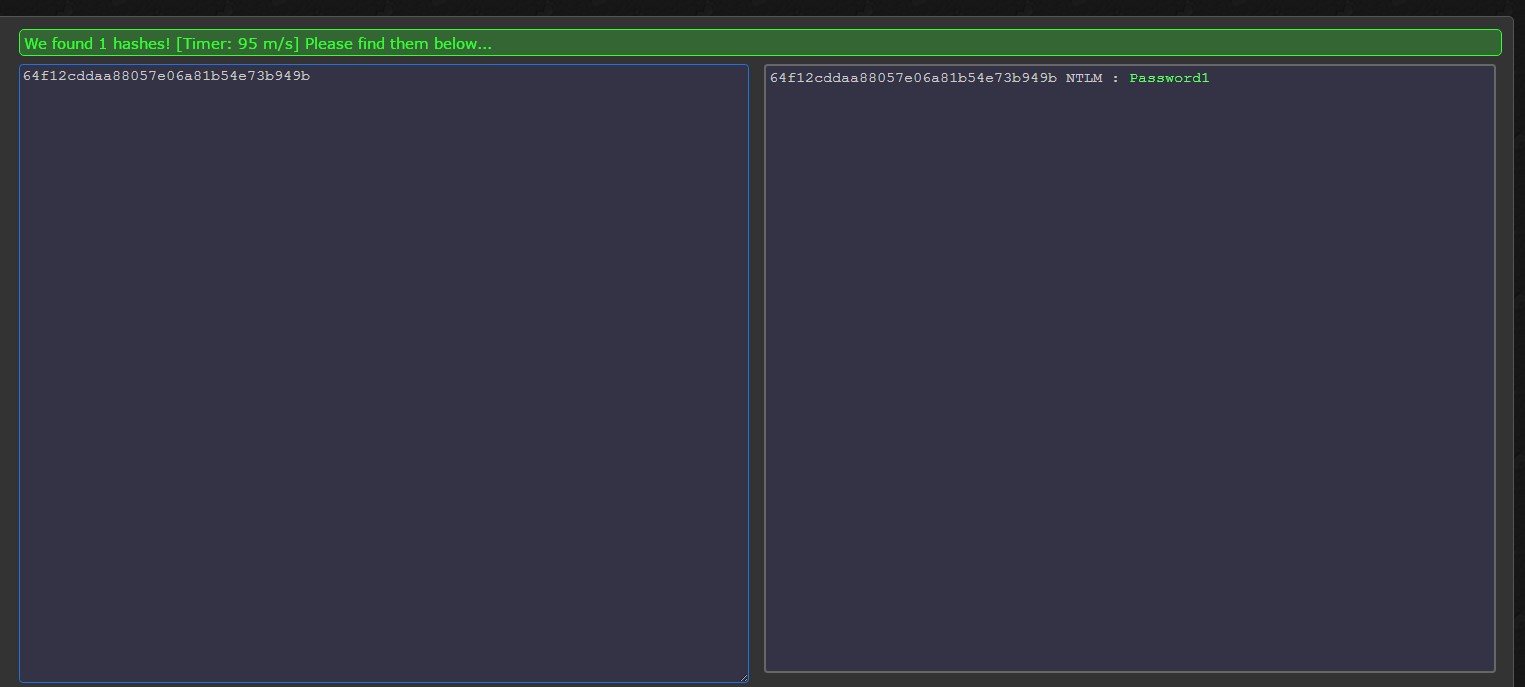
Adding user accounts to Administrators groups (Enterprise Admins, Domain Admins or Administrators) puts the environment at a significant risk because these user accounts can dump all the Active Directory hashes, bypassing all security and auditing mechanisms.
The above process can be used to drastically reduce the number of Admin members.
The hash extraction process is explained d in this article:
https://www.experts-exchange.com/articles/29569/How-to-extract-hashes-from-IFM-backup.html