Auditing domain password hashes is a commonly overlooked but critical requirement to ensuring secure passwords practices are followed.
Methods exist to extract hashes directly for a live domain however this article describes a process to extract user data, including hashes from an IFM backup.
1) Overview
Overpermission and weak/reused passwords are probably the most common security issues found in Active Directory. To address the password issues, it is important to do regular password audits, to address over permissions, see my article about Active Directory delegation.
2) Password Hashes
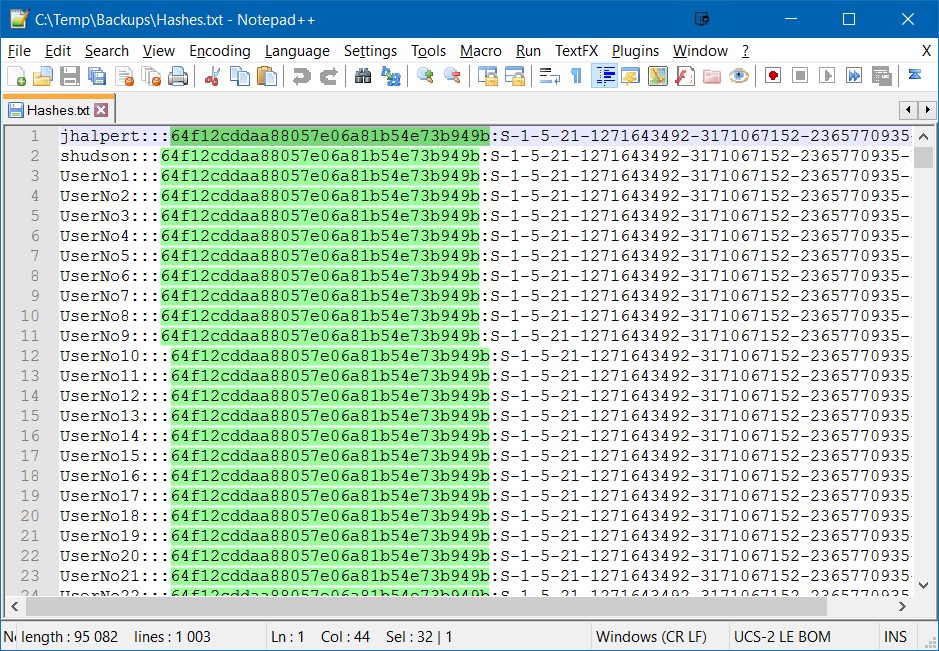
Passwords are stored in Active Directory (NTDS.dit encrypted with a boot key) as an unsalted MD4 hash and as such, to check for password reuse it is a simple case of checking for duplicate hashes in the extracted hashes list.
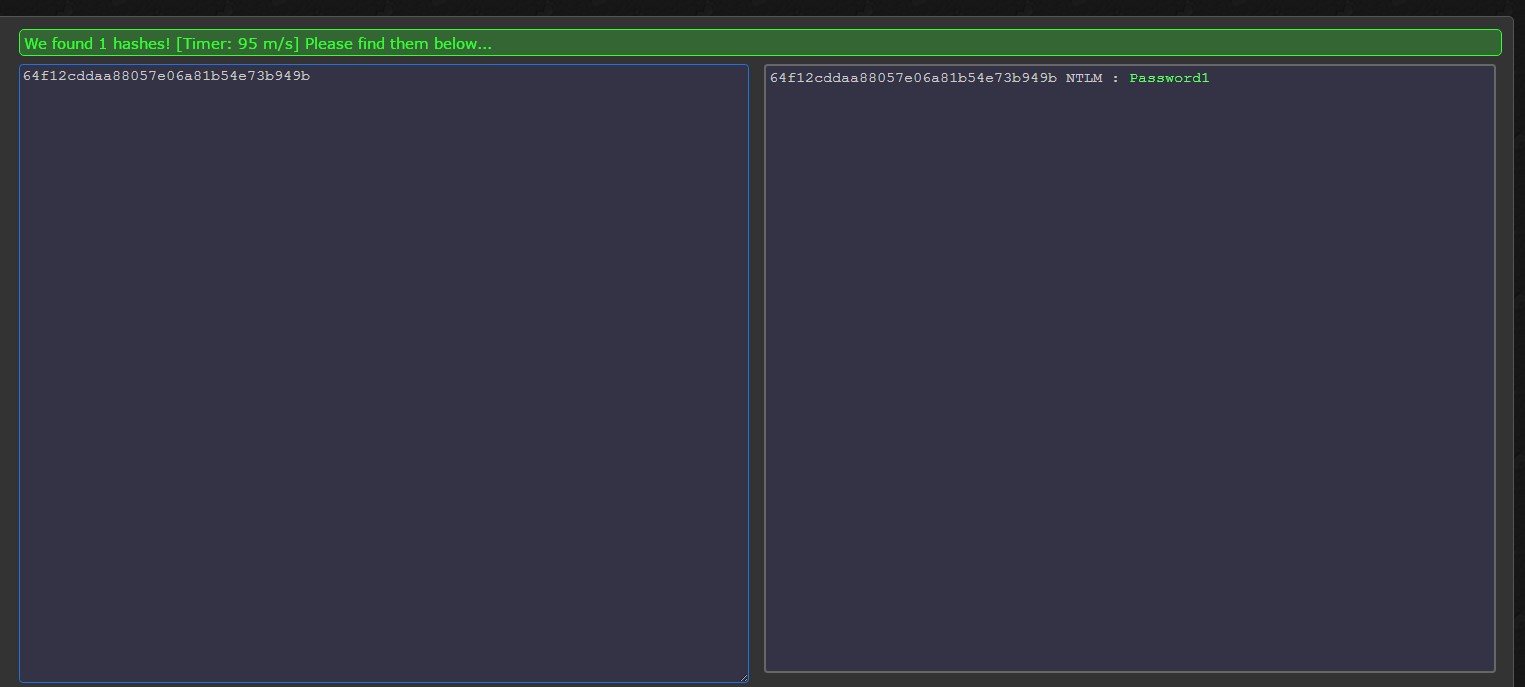
Finding weak passwords are a little trickier. You need to lookup hashes against a rainbow table to ensure you do not have any weak/compromised hashes within your environment.
Both of these are out-of-scope for this article, this article focuses on extracting password hashes.
3) Extracting Password Hashes
a) On a Domain Controller
Start an elevated command prompt and run:
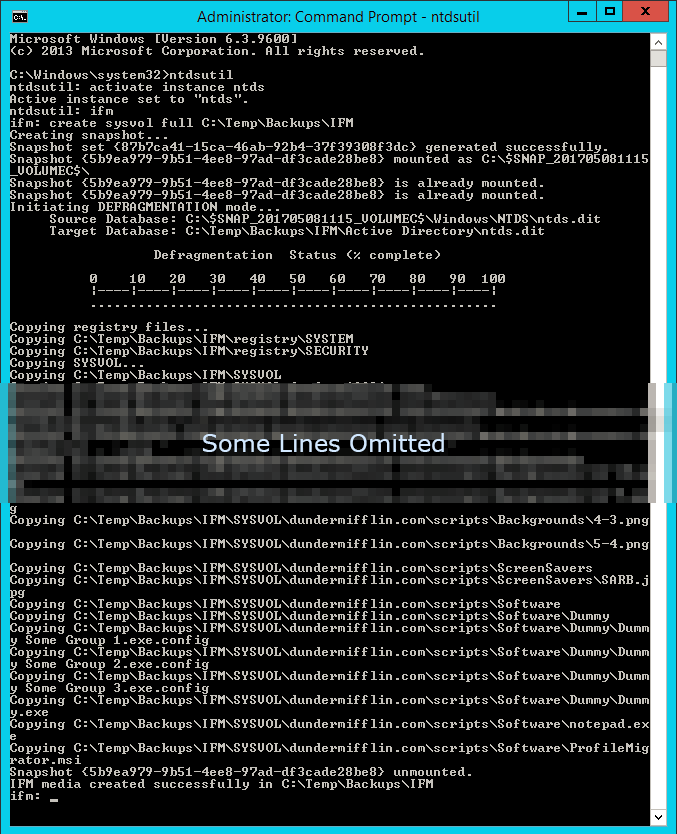
ntdsutil activate instance ntds ifm create sysvol full C:\Temp\Backups\IFM\
Command Output
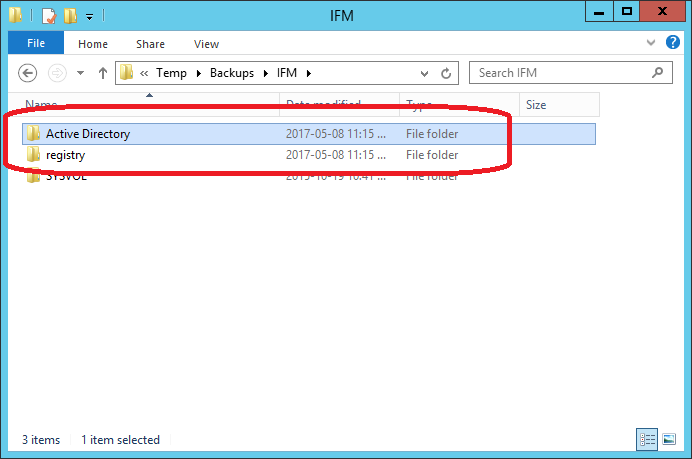
IFM Files
b) On Administrative Computer
Copy the IFM folder and run the following PowerShell script elevated (just copy and paste):
//Download DSInternals from PowerShell Gallery https://www.powershellgallery.com/packages/DSInternals Save-Module -Name DSInternals -path 'C:\temp\DSInternals' //Install DSInternals Install-Module -Name DSInternals //Import DSInternals Module Import-Module DSInternals //Get Boot Key from Registry section of the IFM. If Boot Key is blank, Get-ADDBAccount will still return usernames $key = Get-BootKey -SystemHivePath 'C:\Temp\Backups\IFM\registry\SYSTEM' //Store objects data $hashes = Get-ADDBAccount -All -DBPath 'C:\Temp\Backups\IFM\Active Directory\ntds.dit' -BootKey $key //Convert object data to the desired format $hashes | Format-Custom -View Ophcrack | Out-File C:\Temp\Backups\Hashes.txt
Weak Passwords Found (Getting password from hashes out-of-scope for this article)