Introduction
Active Directory provided a mechanism to set account password via GPO preferences. Unfortunately this was done with an encrypted cpassword value for which the decryption key was published and subsequently the functionality was blocked.
Later, Local Administrator Password Solution (LAPS), was adopted by Microsoft and it is well suited for the task.
The approach described in this article is an alternative method to LAPS which can be used if the schema extension requirement of LAPS cannot be done. It also allows for multiple account management.
For this solution you will need:
- File Share
- SQL Server
- Group Policy
- PasswordImporter
- PasswordViewer
Both PasswordImport and PasswordViewer is available within the same download here
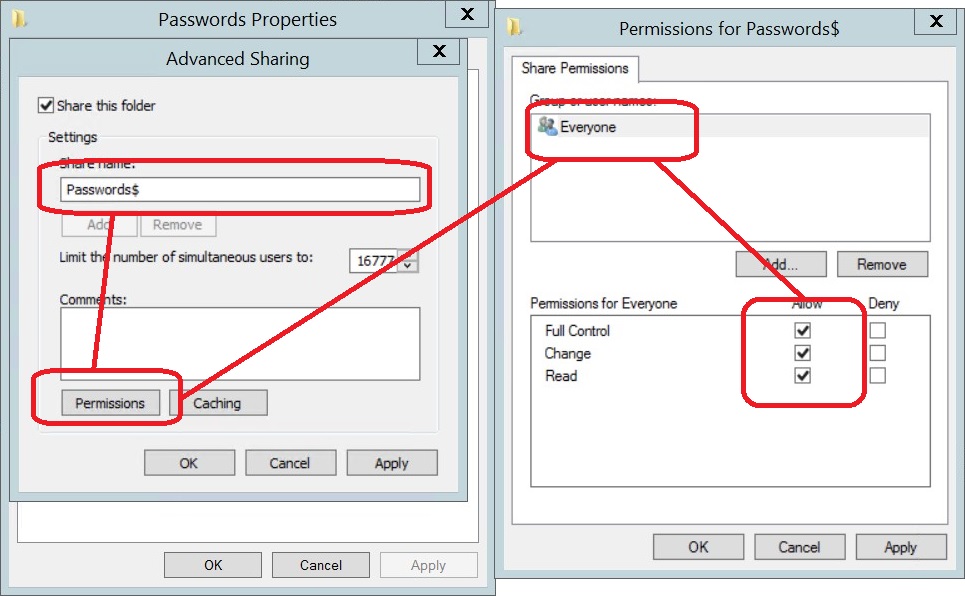
Create share
Create a folder on a server which will hold the passwords reset output files from computers that get the GPO.
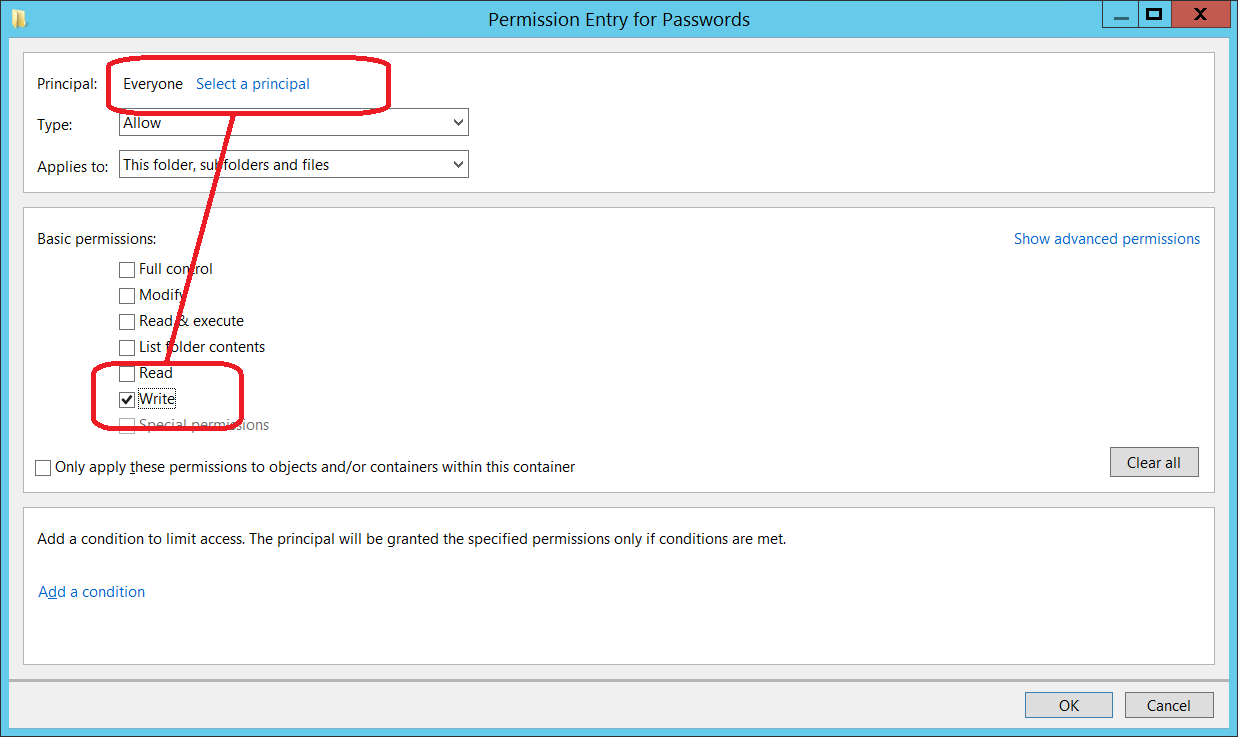
It is important to only allow administrators to view files within this folder. Everyone (authenticated users) should only have create/write permission (as shown below). The reason for this is that password will be stored here in clear-text until the PasswordImporter
tool processed it.
Create GPO
Create a GPO and filter it to the computer objects for the computers you wish to manage passwords for.
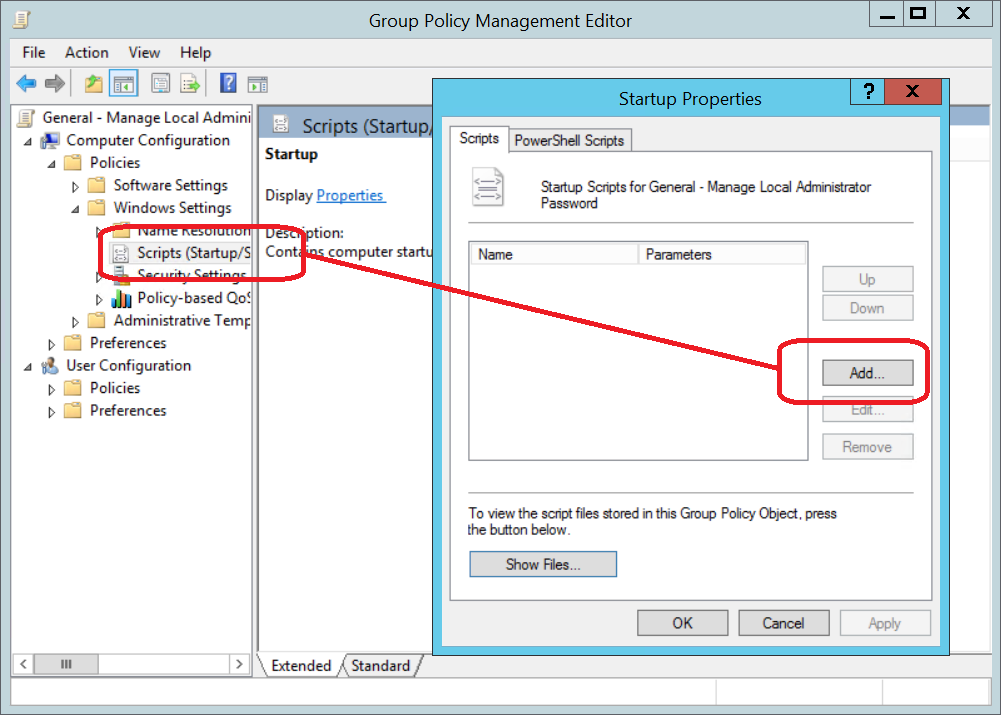
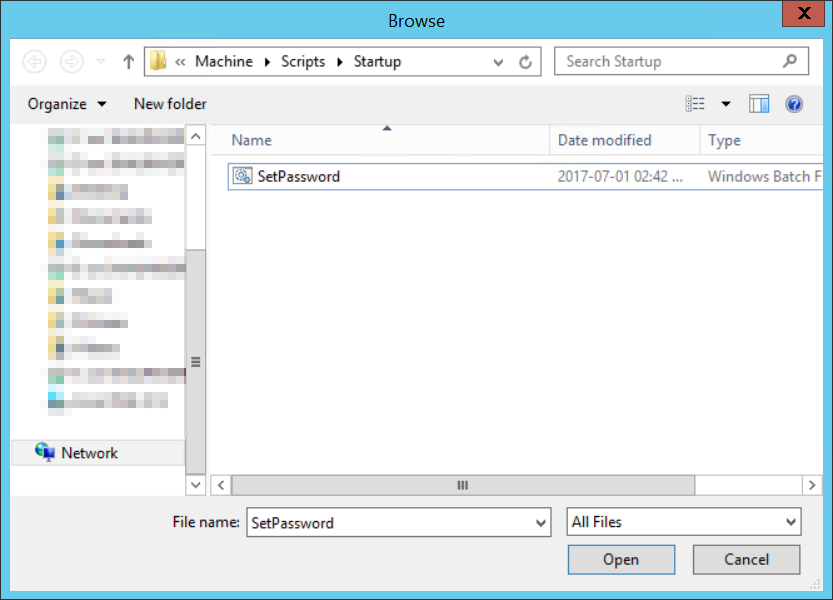
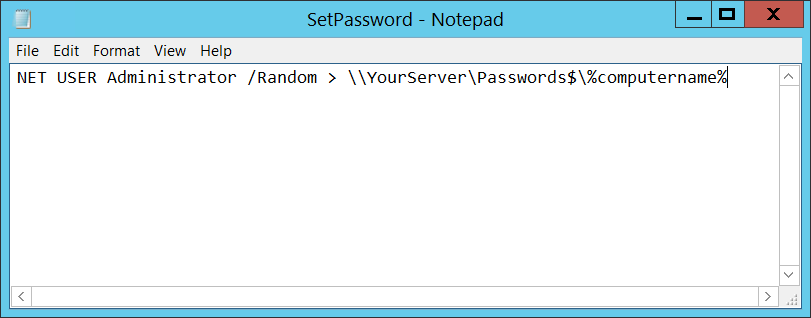
The startup script needs to be set to save password text files to the share created in an earlier step.
Create SQL Table
Use the following SQL script to create a table within SQL to store passwords. Assign a group to this group to SQL and grant it SELECT rights on the Passwords table. Add all your administrators and support personnel into this group.
CREATE TABLE [dbo].[Passwords]( [ID] [int] IDENTITY(1,1) NOT NULL, [ComputerName] [varchar](255) NOT NULL, [Password] [varchar](255) NOT NULL, CONSTRAINT [PK_Passwords] PRIMARY KEY CLUSTERED ( [ID] ASC )WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY] ) ON [PRIMARY]
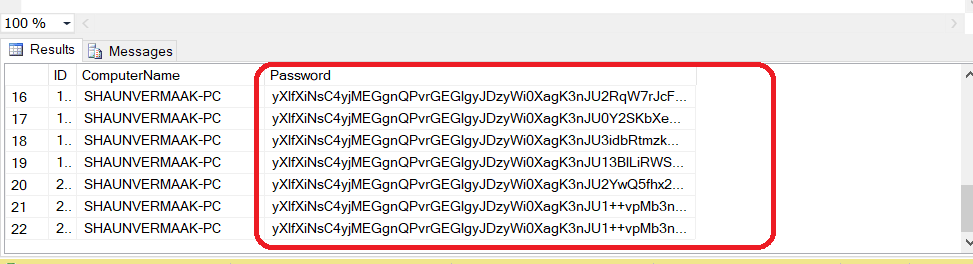
Below is an example of the passwords stored encrypted within SQL
Setup PasswordImporter
PasswordImporter is an application that reads password files from the share and import is, encrypted, into SQL. After a successful import, the password file is deleted.
Open Configurator and specify Location, ConnectionString and LogFile values. Note that Location and ConnectionString needs to be encrypted with encryption key wL!PIQj%EeWj%L^e$nEpdjFzL0d9%Y1#
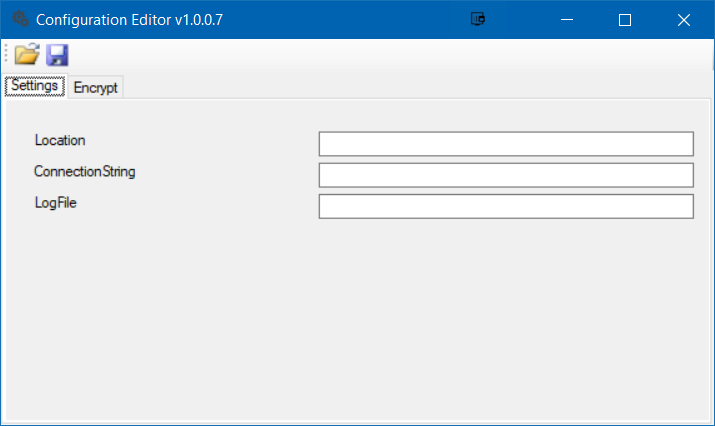
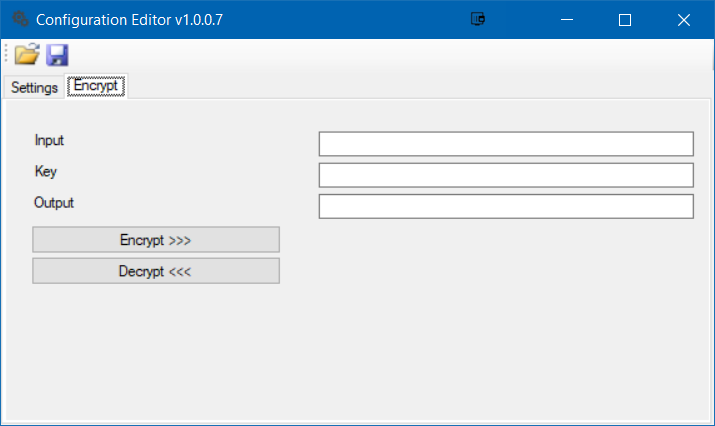
Schedule this application to run every few minutes to import passwords to SQL database
Setup PasswordViewer
PasswordViewer is an application that shows the specified computers password. This application should be distributed to all administrators and support personnel.
Open Configurator and specify FQDN, NetBIOS and ConnectionString values. Note that ConnectionString needs to provide placeholder values for Domain, Username and
Password, for example:
Data source=YOURSQLSERVER;initial catalog=YOURDATABASE;Integrated Security=SSPI; User Id = [DOMAINNAME\USERNAME]; Password = [PASSWORD]